Install Foreman 311 katello rocky9: Difference between revisions
Jump to navigation
Jump to search
| Line 106: | Line 106: | ||
--enable-foreman-cli-katello \ | --enable-foreman-cli-katello \ | ||
--enable-foreman-plugin-ansible \ | --enable-foreman-plugin-ansible \ | ||
--enable-foreman-proxy-plugin-ansible \ | |||
--enable-foreman-plugin-statistics \ | --enable-foreman-plugin-statistics \ | ||
--enable-foreman-plugin-tasks \ | --enable-foreman-plugin-tasks \ | ||
Revision as of 07:09, 7 September 2024
VM SETUP
- CPU: 4
- MEM: 20G
- DISK: 200G
- Host IP: eg: 1.2.3.4
DNS requirements
I use this, because i also stand behind a firewall with loadbalancer and want to use letsencrypt cert for public
- A-Record: eg: foreman01.domain.tld
- CNAME: eg: foreman.domain.tld
- Cert Location: /etc/pki/letsencrypt #keep this place restricted: root.root 0640
wget https://raw.githubusercontent.com/joe-speedboat/linux.scripts/master/shell/openssl_check_cert_chain.sh bash openssl_check_cert_chain.sh /etc/pki/letsencrypt/fullchain.pem 0: subject=CN = foreman.domain.tld issuer=C = US, O = Let's Encrypt, CN = R10 1: subject=C = US, O = Let's Encrypt, CN = R10 issuer=C = US, O = Internet Security Research Group, CN = ISRG Root X1 2: subject=C = US, O = Internet Security Research Group, CN = ISRG Root X1 issuer=C = US, O = Internet Security Research Group, CN = ISRG Root X1 /etc/pki/letsencrypt/fullchain.pem: OK
LINKS
OUTSIDE CONNECTIVITY NEEDS
Install
dnf clean all
dnf -y install https://yum.theforeman.org/releases/3.11/el9/x86_64/foreman-release.rpm
dnf -y install https://yum.theforeman.org/katello/4.13/katello/el9/x86_64/katello-repos-latest.rpm
dnf -y install https://yum.puppet.com/puppet7-release-el-9.noarch.rpm
dnf repolist enabled
dnf -y upgrade
dnf -y install foreman-installer-katello
dnf -y install firewalld
systemctl enable firewalld --now
firewall-cmd \
--add-port="80/tcp" --add-port="443/tcp" \
--add-port="5647/tcp" \
--add-port="8000/tcp" --add-port="9090/tcp" \
--add-port="8140/tcp" \
#--add-port="53/udp" --add-port="53/tcp" \
#--add-port="67/udp" \
#--add-port="69/udp"
firewall-cmd --runtime-to-permanent
firewall-cmd --list-all
public (active)
services: cockpit dhcpv6-client ssh
ports: 80/tcp 443/tcp 5647/tcp 8000/tcp 9090/tcp 8140/tcp
ping -c1 localhost
ping -c1 `hostname -f`
echo "1.2.3.4 foreman01.domain.tld" >> /etc/hosts
echo "1.2.3.4 foreman.domain.tld" >> /etc/hosts
hostnamectl set-hostname `hostname -f`
dnf clean all
dnf makecache
dnf -y upgrade
yum -y install chrony
systemctl start chronyd
systemctl enable chronyd
echo sources | chronyc
reboot
Setup Foreman
foreman-installer --scenario katello \ --foreman-servername foreman.domain.tld \ --foreman-foreman-url https://foreman.domain.tld \ --foreman-unattended-url https://foreman.domain.tld \ --foreman-proxy-foreman-base-url https://foreman.domain.tld \ --foreman-proxy-registered-name foreman.domain.tld \ --foreman-proxy-registered-proxy-url https://foreman.domain.tld:9090 \ --foreman-proxy-puppet-url https://foreman.domain.tld:8140 \ --puppet-server-foreman-url https://foreman.domain.tld \ --foreman-proxy-template-url http://foreman.domain.tld:8000 \ --foreman-proxy-trusted-hosts foreman.domain.tld \ --foreman-proxy-trusted-hosts foreman01.domain.tld \ --foreman-initial-organization "BITBULL" \ --foreman-initial-location "Core" \ --foreman-initial-admin-username admin \ --foreman-initial-admin-password change-me-here \ --enable-foreman-cli-ansible \ --enable-foreman-cli \ --enable-foreman-cli-katello \ --enable-foreman-plugin-ansible \ --enable-foreman-proxy-plugin-ansible \ --enable-foreman-plugin-statistics \ --enable-foreman-plugin-tasks \ --certs-server-cert "/etc/pki/letsencrypt/cert.pem" \ --certs-server-key "/etc/pki/letsencrypt/key.pem" \ --certs-server-ca-cert "/etc/pki/letsencrypt/fullchain.pem" hammer settings list | grep foreman01 echo "CTRL-C to abort" sleep 10 hammer settings set --id foreman_url --value https://foreman.domain.tld cd $HOME/bin wget https://raw.githubusercontent.com/joe-speedboat/linux.scripts/master/shell/ssl_cert_scanner.sh vim ssl_cert_scanner.sh PORTS="23443 443 5432 61613 6379 80 8005 9090" WAIT_SEC=1 IP_RANGES=' foreman01.domain.tld foreman.domain.tld 127.0.0.1 ' bash ssl_cert_scanner.sh
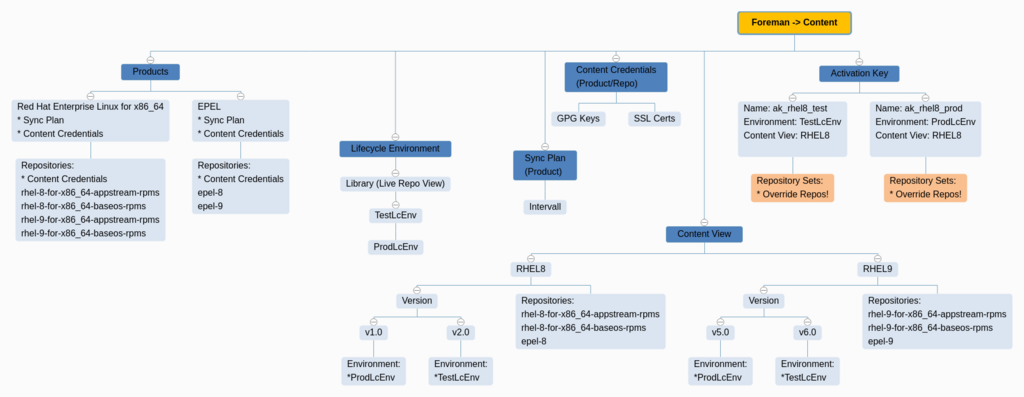
Foreman Content Management - Menu Overview
Manage Repos with Foreman
- https://opensource.com/article/21/9/centos-stream-foreman
- https://www.youtube.com/watch?v=XsCi9Jy2lGs&t=3s
Create Content
Sync Plan
- Content > Sync Plans
- Create Sync Plan > Daily
Products/Repos
Rocky 9
- Content > Products > Repo Discovery
- Type: Yum Repositories
- URL to Discover: https://pkg.adfinis.com/rockylinux/9/
- Filter: /9/AppStream/x86_64/os/
- Filter: /9/BaseOS/x86_64/os/
- Filter: /9/BaseOS/x86_64/kickstart/
- Name: Rocky Linux
- Add "Rocky Linux 9" in front of suggested Repository Name
- Run Repository Creation
- Products > Rocky Linux
- Sync Plan: Daily
- Products > Rocky Linux > Repositories: ALL
- Restrict to architecture: x86_64
EPEL 9
- Content > Products > Create
- Name: EPEL
- Sync Plan: Daily
- Repositories > New Repositoriy
- Type: yum
- Name: epel-el9
- Restrict to Architecture: x86_64
- Upstream url: https://pkg.adfinis.com/epel/9/Everything/x86_64/
- Save
Lifecycle Environment
- Content > Lifecycle Environment > Create
- TestLcEnv > ProdLcEnv
Content View
Remind to sync all Repos before proceeding with this steps
- Content > Content views > Create
- Name: cv_rocky9
- Solve dependencies: TRUE
- CV: cv_rocky9 > TAB:Repositories
- Add: all except Kickstart (think)
- Content > Content views > cv_rocky9 > Publish new version
- Promote: TRUE
- Version: 1.0
- Env: TestLcEnv + ProdLcEnv
Activation Keys
- Content > Activation Keys > Create
- Name: ak_rocky9_test
- Environment: TestLcEnv
- Content View: cv_rocky9
- Repository Sets: Disable all but needed
- Content > Activation Keys > Create
- Name: ak_rocky9_prod
- Environment: ProdLcEnv
- Content View: cv_rocky9
- Repository Sets: Disable all but needed
Register System
- Hosts > Register Host > select needed settings
- Copy-Paste Register info to root on target system
Disable Default Repos
curl https://raw.githubusercontent.com/joe-speedboat/linux.scripts/master/shell/foreman_host_disable_default_repos.sh | bash
Patch Cycle Ideas Brainstorming
Prerequisites
- Daily Sync of all Foreman Libraries (Product upstream Repos)
- Working Repos as mentioned above
- Systems are grouped and registered in Lifecycle Environments
- TEST
- TEST-LATE
- PROD
- PROD-LATE
The meaning of "LATE" is to patch this systems later to avoid production issues (eg: half of the systems of a Cluster (DNS, Web, ...)
Patch Cycle
- All systems get patched at least every 4 weeks
- A Rundeck Job does update the Content Views on a regular base.
EXAMPLE: ---------------------------------- KW01 -> "Library" (daily sync) into "TEST" Content View as Version "KW01" KW02 -> Version "KW01" into "TEST-LATE" Content View KW03 -> Version "KW01" into "PROD" Content View KW04 -> Version "KW01" into "PROD-LATE" Content View KW05 -> "Library" (daily sync) into "TEST" Content View as Version "KW05" KW06 -> Version "KW05" into "TEST-LATE" Content View KW07 -> Version "KW05" into "PROD" Content View KW08 -> Version "KW05" into "PROD-LATE" Content View ...
Emergency Patching
Due security needs, it may be necessary to apply patches immediatly. For that, you have several options
Add Packages to Conent View
- Create a custom Repository eg. "Rocky9 Custom"
- Add RPMS, which are newer and needed for emergency patching to this repo
- They get applied with Ansible on a daily base during patch cycle
- Once they get obsolete (regular Repo gets updated) you can purge them out of the repo
Update Conent View
Easiest way to update repos but may apply more updates than needed for security reason
- Needs to pause the automated "Content View" update in Rundeck
Manual Update
Manually Update custom packages with yum/dnf on affected systems
- least prefered, due missing overview
TIPPS AND TRICKS
- Push Host Package State to Foreman
subscription-manager repos --list